Lynis is an open source security auditing tool . Primary goal is to help users with auditing and hardening of Unix and Linux based systems...


Lynis is an open source security auditing tool . Primary goal is to help users with auditing and hardening of Unix and Linux based systems...

Nmap is a utility for port scanning large networks, although it works fine for single hosts. Sometimes you need speed, other times you may ...

New Acrylic WiFi software update. WiFi software for network analysis has gone through many changes since the first free version and final...
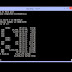
Use BIOS ram hacks to make a SSH server out of any INT 10 13h app (MS-DOS is one of those) You can find a demo Youtube Video here below: Dow...
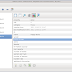
Mobius Forensic Toolkit is a forensic framework written in Python/GTK that manages cases and case items, providing an abstract interface f...

CipherShed is free (as in free-of-charge and free-speech ) encryption software for keeping your data secure and private. It started as a f...

Viproy Voip Pen-Test Kit provides penetration testing modules for VoIP networks. It supports signalling analysis for SIP and Skinny protoco...

A simple tool that allows users to have strong unique passwords for each website, without the need to store them either locally or with an o...

SearchMyFiles is an alternative to the standard "Search For Files And Folders" module of Windows. It allows you to easily search ...

WAF-FLE is a OpenSource ModSecurity Console, allows modsecurity admin to store, view and search events sent by sensors using a graphical d...

GnuPG is a complete and free implementation of the OpenPGP standard as defined by RFC4880 (also known as PGP ). GnuPG allows to encrypt and...

FBCacheView is a simple tool that scans the cache of your Web browser (Internet Explorer, Firefox, or Chrome), and lists all images displa...

The Tor software protects you by bouncing your communications around a distributed network of relays run by volunteers all arou...

Netsparker Web Application Security Scanner can find and report web application vulnerabilities such as SQL Injection and Cross-site Scrip...

The swiss army knife of PDF Analysis Tools. Based on peepdf - http://peepdf.eternal-todo.com . Features Interactive Console: Type "hel...

The Suricata Engine is an Open Source Next Generation Intrusion Detection and Prevention Engine . This engine is not intended to just repla...

The Samhain host-based intrusion detection system (HIDS) provides file integrity checking and log file monitoring/analysis , ...

SimpleProgramDebugger is a simple debugging tool for Windows that attaches to existing running program or starts a new program in debuggin...

PWGen is a professional password generator capable of creating large amounts of cryptographically- secure passwords or passphrases consis...

XCat is a command line program that aides in the exploitation of blind XPath injection vulnerabilities. It can be used to retrieve the whole...
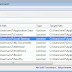
Starting from Windows Vista, Microsoft uses symbolic links and junction points of NTFS file system in order to make changes in the folders...

Shellter is a dynamic shellcode injection tool, and probably the first dynamic PE infector ever created. It can be used in order to inject s...

Magic Unicorn is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. Based on Matthew Graeber...
HoneyDrive is the premier honeypot Linux distro. It is a virtual appliance (OVA) with Xubuntu Desktop 12.04.4 LTS edition installed. It co...