Tcpcrypt is a protocol that attempts to encrypt (almost) all of your network traffic. Unlike other security mechanisms, Tcpcrypt works out ...


Tcpcrypt is a protocol that attempts to encrypt (almost) all of your network traffic. Unlike other security mechanisms, Tcpcrypt works out ...

Router Post-Exploitation Framework Currently, the framework includes a number of firmware image modules: 'Verified' - This module ...

CeWL is a ruby app which spiders a given url to a specified depth, optionally following external links, and returns a list of words which ...

John the Ripper is a free password cracking software tool. Initially developed for the Unix operating system, it now runs on fifteen differ...

Android Studio is the official IDE for Android application development, based on IntelliJ IDEA . On top of the capabilities you expect from ...
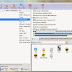
AutoScan-Network is a network scanner (discovering and managing application). No configuration is required to scan your network . The ...

A very fast network logon cracker which support many different services. See feature sets and services coverage page - incl. a speed compa...

This is a mini-firewall that completely isolates a target device from the local network. This is for allowing infected machines Internet acc...

An open source memory analysis tool built on top of Volatility. It is meant as a proving ground for interesting new techniques to be made ...

Sparty is an open source tool written in python to audit web applications using sharepoint and frontpage architecture. The motivation behind...

As penetration testers, it’s crucial to identify what types of attacks are detected and what’s not. After running into a recent penetrati...

Pompem is an open source tool, which is designed to automate the search for exploits in major databases. Developed in Python, has a system o...

r2 is a rewrite from scratch of radare in order to provide a set of libraries and tools to work with binary files This is the rewrite of rad...

Webfwlog is a flexible web-based firewall log analyzer and reporting tool. It supports standard system logs for linux, FreeBSD, OpenB...

WAP 2.0 is a source code static analysis and data mining tool to detect and correct input validation vulnerabilities in web applications...

ZMap is an open-source network scanner that enables researchers to easily perform Internet-wide network studies. With a single machine and...

MLDonkey is a multi-platform and freely distributed eDonkey client, a P2P (Peer-to-Peer) file-sharing application. It provides users with b...

Tor 0.2.5.10 is the first stable release in the 0.2.5 series. It adds several new security features, including improved denial-of-service r...

Tor 0.2.5.10 is the first stable release in the 0.2.5 series. It adds several new security features, including improved denial-of-servi...