How it works Scan the networks. Select network. Capture handshake (can be used without handshake) We choose one of several web interfaces ta...


How it works Scan the networks. Select network. Capture handshake (can be used without handshake) We choose one of several web interfaces ta...

Wifiphisher is a security tool that mounts fast automated phishing attacks against WiFi networks in order to obtain secret passphrases and ...

Faraday introduces a new concept (IPE) Integrated Penetration-Test Environment a multiuser Penetration test IDE. Designed for distribution,...

SPARTA is a python GUI application which simplifies network infrastructure penetration testing by aiding the penetration tester in the sca...

A bash script to automate the most basic usage of LUKS volumes in Linux. Like: Creating a virtual disk volume with LUKS format. Mounting an ...

Tcpcrypt is a protocol that attempts to encrypt (almost) all of your network traffic. Unlike other security mechanisms, Tcpcrypt works out ...

Blue Maho is GUI-shell (interface) for suite of tools for testing security of bluetooth devices. It is freeware, opensource, written on py...

Router Post-Exploitation Framework Currently, the framework includes a number of firmware image modules: 'Verified' - This module ...

CeWL is a ruby app which spiders a given url to a specified depth, optionally following external links, and returns a list of words which ...

John the Ripper is a free password cracking software tool. Initially developed for the Unix operating system, it now runs on fifteen differ...

PuttyRider injects a DLL into a running putty.exe process in order to sniff all communication and inject Linux commands on the remote server...

Snort is the most powerful IPS in the world, setting the standard for intrusion detection. So when we started thinking about what the next g...

Android Studio is the official IDE for Android application development, based on IntelliJ IDEA . On top of the capabilities you expect from ...

This tool finds undocumented and secret commands implemented in a smartcard. An instruction is divided into Class (CLA), Instruction-Number ...
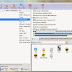
AutoScan-Network is a network scanner (discovering and managing application). No configuration is required to scan your network . The ...

A very fast network logon cracker which support many different services. See feature sets and services coverage page - incl. a speed compa...

The Samurai project team is happy to announce the release of a development version of the Samurai Web Testing Framework. Th...

This is a mini-firewall that completely isolates a target device from the local network. This is for allowing infected machines Internet acc...

What is Cuckoo Sandbox? In three words, Cuckoo Sandbox is a malware analysis system. What does that mean? It simply means that you can throw...
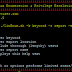
LinEnum will automate many of the checks that I’ve documented in the Local Linux Enumeration & Privilege Escalation Cheatsheet . It’s...