TCHead is software that decrypts and verifies TrueCrypt headers.
TCHead supports all the current hashes, individual ciphers, standard
volume headers, hidden volume headers and system drive encrypted headers
(preboot authentication).
Brute-force TrueCrypt : However, TrueCrypt passwords go through
many iterations and are strengthened. Cracking them takes time. Very
strong passwords will not be cracked. Also, in addition to trying
multiple passwords an attacker must try each password against each
combination of hash and cipher (assuming they do not know what these are
beforehand). System encrypted hard drives use only one hash and cipher,
so attacking those is faster.
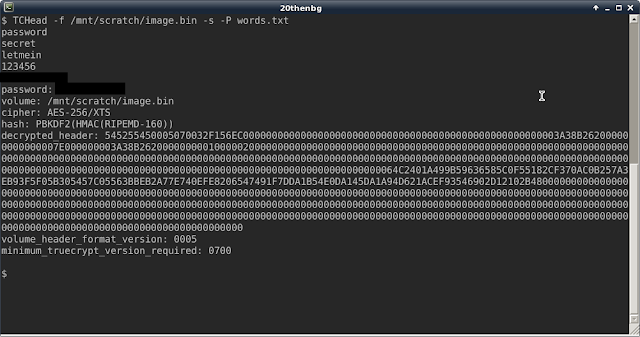
Testing TCHead: Create a TrueCrypt volume using the default hash
and cipher (RIPEMD-160 and AES), set the password to "secret", then run
TCHead against it like this and it will decrypt the header (provided
that the word "secret" is in the word list)
Command : TCHead -f name_of_volume.tc -P words.txt
Decrypt hidden volumes:
Command : TCHead -f name_of_volume.tc -P words.txt --hidden
Multiple passwords (brute-force): Create or download a list of
words in a text file (one word per line) using words that you think are
likely to decrypt the header, then run TCHead against it like this. If
the correct password is found, the header will be decrypted:
Command : TCHead -f name_of_volume.tc -P words.txt